This article explains
- The different WIDS and WIPS features supported through Aruba Central dashboard.
- Configuration of these features through the Central dashboard.
You can configure the following options under WIDS/WIPS for an IAP through the Central dashboard:
Intrusion Detection:
- Infrastructure Detection Policies— Specifies the policy for detecting wireless attacks on access points
- Client Detection Policies— Specifies the policy for detecting wireless attacks on clients
The following levels of INTRUSION DETECTION can be configured in the Wireless IDS/IPS
page on the Central dashboard:
- Off
- Low
- Medium
- High
- Custom
Intrusion Prevention:
- Infrastructure Protection Policies— Specifies the policy for protecting access points from wireless attacks.
- Client Protection Policies— Specifies the policy for protecting clients from wireless attacks.
- Containment Methods— Prevents unauthorized stations from connecting to your Instant network.
The following levels of INTRUSION PROTECTION can be configured in the Wireless IDS/IPS
page on the Central dashboard:
Note: Please refer to the Instant User Guide for the detailed list of default policies supported under each level.
Environment : This article applies to all the Instant Access Points running Aruba Instant OS version 6.2.1.0-3.3.0.0 or above and managed by Aruba Central.
Configuring Intrusion Detection on Aruba Central:
- Navigate to Configuration> Network
- Choose the group in which the configuration needs to be applied.
- Click Wireless IDS/IPS
- Click “Detection”.
- Choose your threat detection level for infrastructure and client. You can also choose the “custom” option to specify the custom defined detection policy.
- Click “Save Settings” at the bottom of the page.
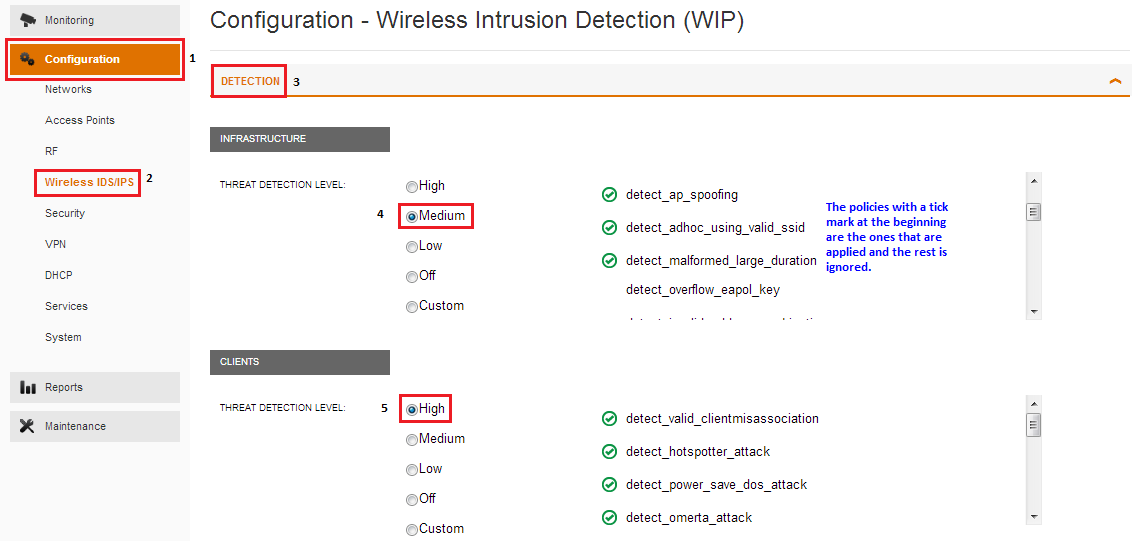
The following screenshot shows the above configuration. In this screenshot, the Infrastructure detection policy level is set to ‘Medium’ and the Client detection policy level is set to ‘High’ and all the associated policies appear on the right.
Configuring Intrusion Prevention on Aruba Central:
- Navigate to Configuration> Network
- Choose the group in which the configuration needs to be applied.
- Click Wireless IDS/IPS
- Click “Protection”.
- Choose the containment method for wired and/or wireless.
- Wired containment: When enabled, Aruba Access Point generates ARP packets on the wired network to contain wireless attacks.
- Wireless containment: When enabled, the system attempts to disconnect all clients that are connected or attempting to connect to the identified Access Point. Wireless containment can be of following types:-
- None— Disables all the containment mechanisms.
- Deauthenticate only— With deauthentication containment, the Access Point or client is contained by disrupting the client association on the wireless interface.
- Tarpit containment— With Tarpit containment, the Access Point is contained by trapping clients that are attempting to associate with it to a tarpit. The tarpit can be on the same channel or a different channel as the Access Point being contained. We can either trapit only the invalid stations or all the stations.
6. Click “Save Settings” at the bottom of the page.
The following screenshot shows the above configuration. In this screenshot, the Infrastructure protection policy is set to ‘Low’ and the Client protection policy is set to ‘High’ and all the associated policies appear on the right.