Overview
A RADIUS server such as ClearPass can be used to control what commands an authenticated user can run on the CLI of that switch. Different users or user groups can be assigned granular access to CLI commands, based on white or black lists.
How it works
When the NAS (switch) sends the RADIUS server a valid user name and password, the RADIUS server (ClearPass) sends an Access-Accept packet that contains two additional attributes (command list and the command exception flag). When an authenticated user enters a command on the switch, the switch checks whether the user has permission to execute that command.
After the Access-Accept packet is delivered, the command list resides on the switch. Any changes to the user's command list on the RADIUS server are not seen until the user is authenticated again.
The table "HPE command string and exception" in the Access Security Guide shows how to combine the HP-Command-String and HP-Command-Exception attributes for various outcomes.
Process
This document assumes a working ClearPass and switch configuration, with switch logins already authenticated by RADIUS, and focusses on the additional config to enable command authorisation. It extends and updates Jamie's "HPE Switch Management Authentication with ClearPass".
Switch Configuration
The key additional command on the switch is:
aaa authorization commands radius
You may want to keep an SSH session open on the switch as you test to make sure you don't lock yourself out.
ClearPass Configuration
Preparation
Make sure you have the latest RADIUS dictionary installed for Hewlett Packard Enterprise (31 or more entries). CPPM:Administration\Dictionaries\RADIUS
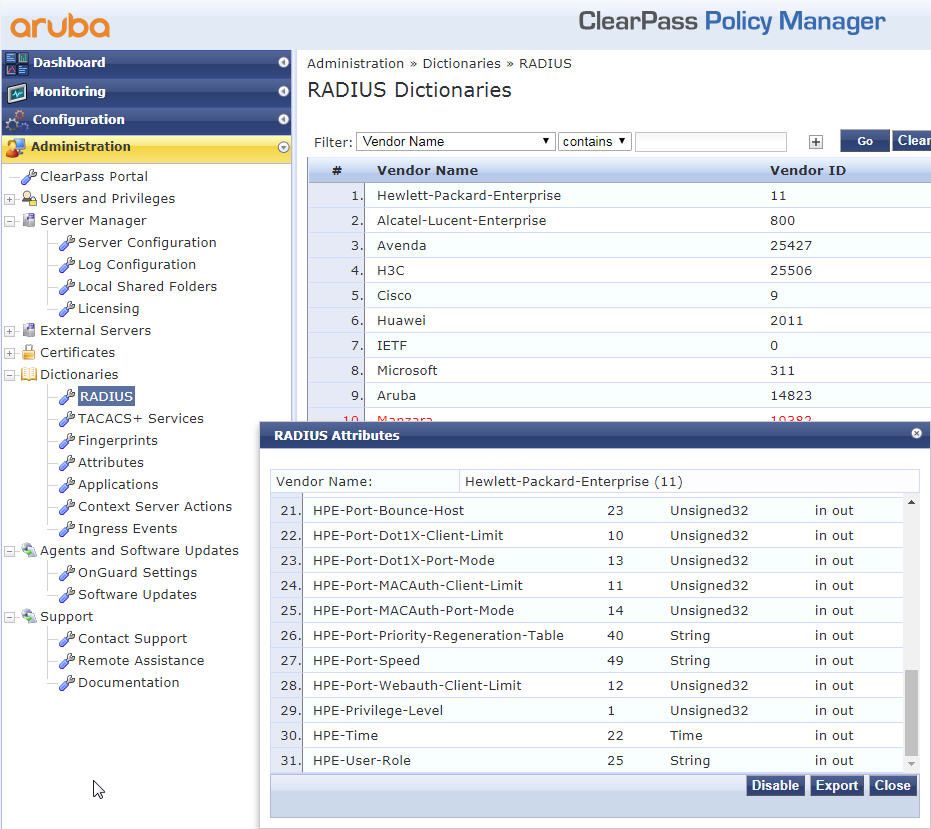
Existing Service
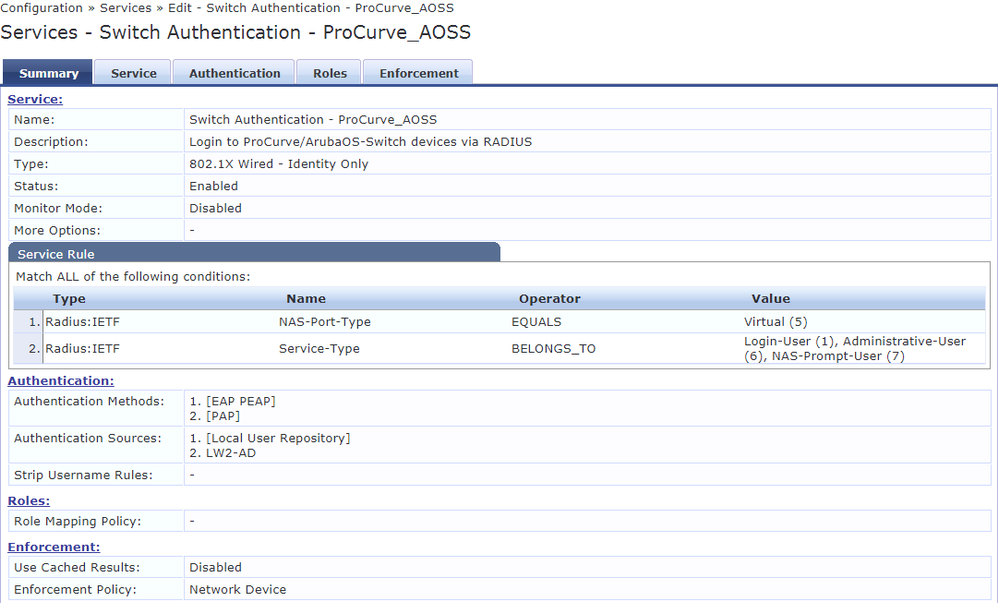
I already had the Service "Switch Authentication - ProCurve_AOSS" for RADIUS logins to switches.
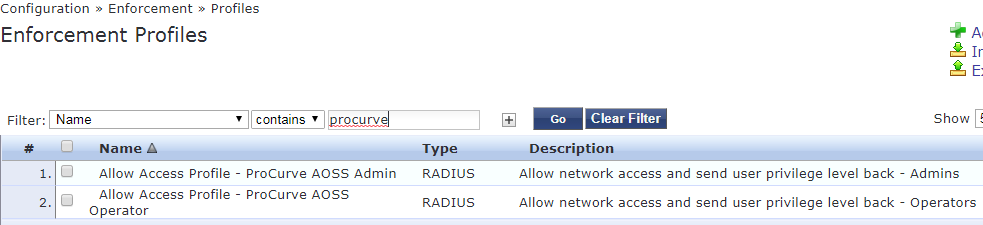
Enforcement Profile
The existing profile was renamed to "Allow Access Profile - ProCurve AOSS Admin", and an additional profile created "Allow Access Profile - ProCurve AOSS Operator"
The admin profile needed to be modified to enable all commands to be run (otherwise the login would not complete). All commands will run except those listed (and none are listed).
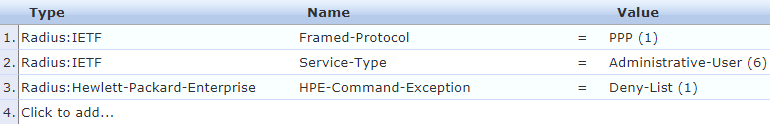
The operator profile has a much more restrictive set of commands. Only the commands in the list will run:
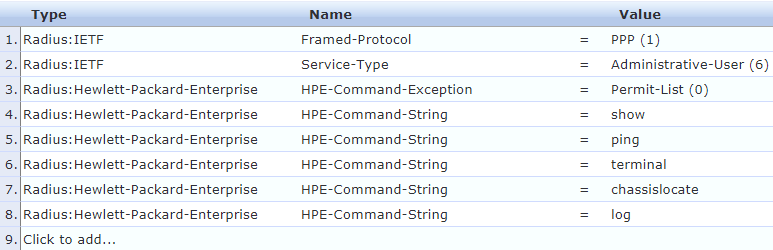
These enforcement profile need to be linked in the Service.
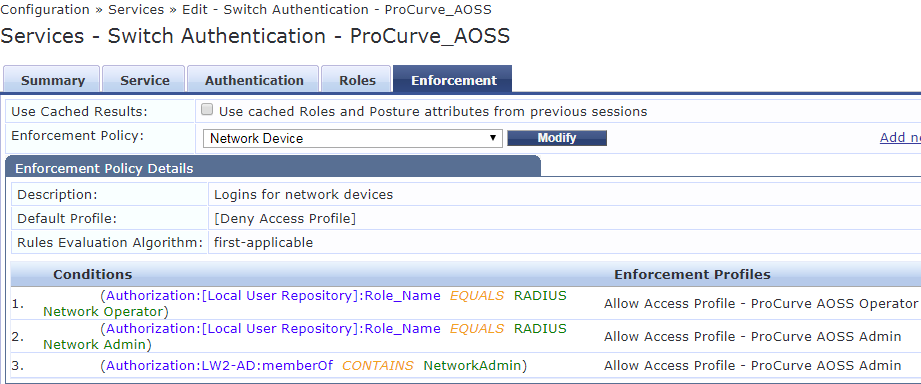
Testing
Admin Group User
Logged in as "nadmin", a member of network admins group
bvcore01# conf
bvcore01(config)#
Successful login and full access to all commands.
Operator Group User
Logged in as "operator1", a member of the operators group
bvcore01# conf
Not authorized to execute this command.
bvcore01# sh ver
Image stamp:
/ws/swbuildm/maint_spokane_qaoff/code/build/btm(swbuildm_maint_spokane_qaoff_ma
int_spokane)
Dec 21 2017 21:31:18
K.16.02.0022m
435
Boot Image: Primary
Boot ROM Version: K.15.30
bvcore01# chassislocate blink 1
bvcore01# ssh 172.20.100.9
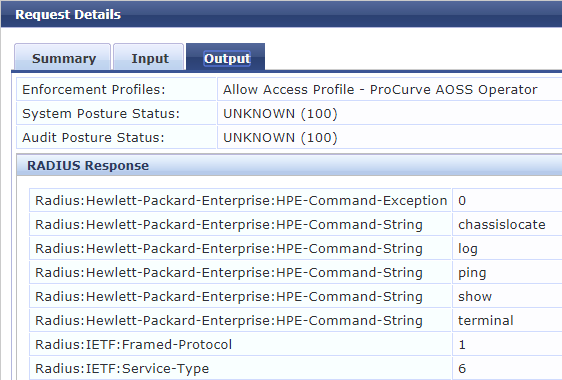
Not authorized to execute this command.Only commands in the enforcement profile for operators are able to run.
The Access Tracker view
Console
Currently not configured for RADIUS login, so you can always connect with a serial console cable.
References