Private VLANs are a great way to segregate existing VLANs into
multiple sets of ports to isolate traffic. Today I’m going to show how to configure Isolated VLANs within private VLANs so devices connected to switch ports cannot exchange traffic. Traffic coming into an isolated port can only go out through an Uplink to the Primary VLAN. The primary VLAN is used to forward frames downstream to the Isolated VLANS.
For environments that house boarding students this is a great way to ensure malicious activity can’t be undertaken on the LAN side of the environment. The diagram below depicts a sample of how isolated port traffic traverses the network.
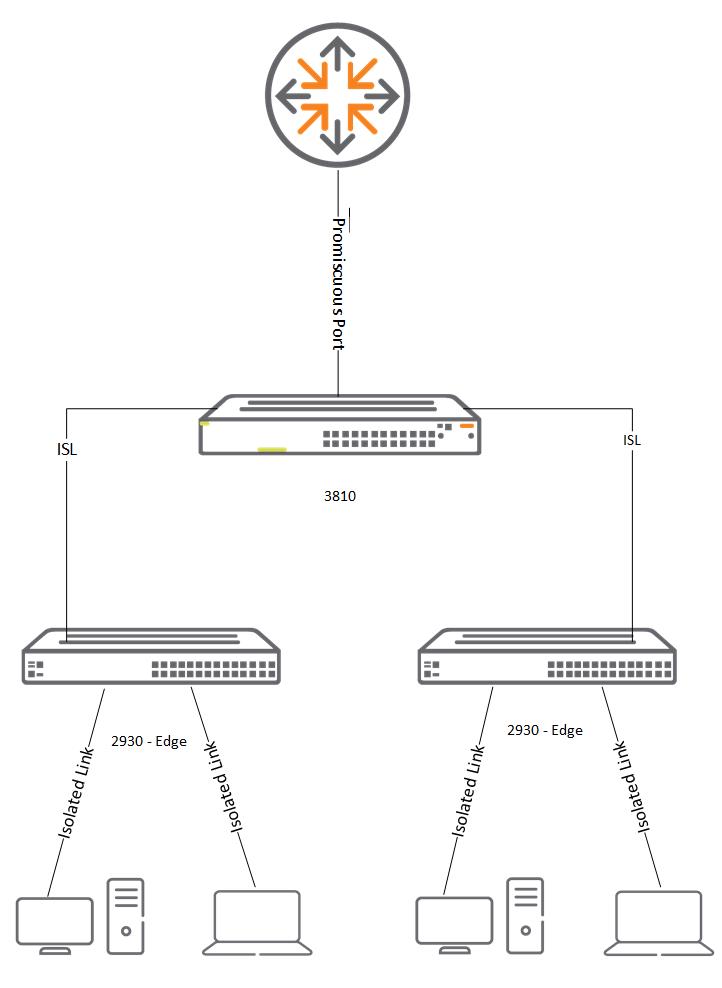
Initially a Primary VLAN needs to be created on the edge switch. In this example VLAN 110 is the Primary VLAN
3810(config)#vlan 110 private-vlan primary
A promiscuous port in the private VLAN on the edge switch is then required. This is where the isolated VLAN traffic will be sent out to the network.
38100(config)# interface 1 private-vlan promiscuous
Then add the promiscuous port to the primary VLAN.
2930(config)# vlan 110 tagged 1
Create and Associate the secondary VLAN to the primary VLAN
2920(config)# vlan 110 private-vlan isolated 120
Add isolated edge ports (device connected ports) to the Private VLAN. In this case port 2. ArubaOS switches also support dynamic VLANs if you want to dynamically assign isolated VLANs to switch ports
2930(config)#vlan 120 untagged 2
ISL configuration (Between the 3810 and 2930)
Add the Private VLAN port member across both switches (ISL port), for example port 4.
3810(config)# no interface 4 private-vlan promiscuous
3810(eth-2)#vlan 110 tagged 4
2930(config)# no interface 4 private-vlan promiscuous
2930(eth-2)#vlan 110 tagged 4
Additional NOTES:
- Existing VLANS cannot be configured as Secondary VLANS.
- Community/Isolated ports must be untagged on 2920 switches. On other platforms (5400, 3800, 5400R and 3810), the access ports can be either untagged or tagged members.
- You Cannot create more than one isolated VLAN under a primary VLAN. If as per the above configuration, you need another Secondary Isolated VLAN, it will have to be associated with a Different Primary VLAN. See the example below.
The configuration should look like this.
2930(config)#show run vlan 110
Running configuration:
vlan 110
name "VLAN110"
private-vlan primary
private-vlan isolated 120
tagged 4
no ip address
exit
vlan 120
name "VLAN120"
untagged 2
no ip address
exit
3810(config)#show run vlan 110
Running configuration:
vlan 110
name "VLAN110"
private-vlan primary
private-vlan isolated 120
tagged 4
no ip address
exit
vlan 120
name "VLAN120"
no ip address
exit
The following commands can be used to verifying configuration:
2930(vlan-110)# show private-vlan promiscuous-ports
2930(config)#show vlans 120 private-vlan
Further information regarding the configuration of private VLANs can be found in the relevant advanced traffic management guide for the relevant switches below:
http://h20566.www2.hpe.com/portal/site/hpsc/?cc=au&lang=en-au&ac.admitted=1438571778305.125225703.1938120508