A whie ago i saw a good article on microsoft blog which does refer to this
Many of us does think that by hidding the SSID its a security feature when its not. The SSID was not designed to be hidden, so it wont provide you security.
We all know that finding a SSID is an easy task. You can always use Network stumbler, or other tools like this, and you will find it
When you hide your SSID and you click in here
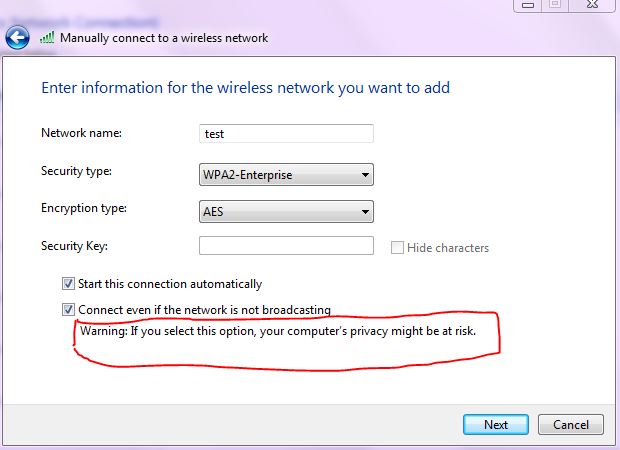
Connect even if the network is not broadcasting and it tells you warning you can put your privacy at risk and thats exactly what happens
So what will happen is that your laptop or iphone or whatever device will try to keep connecting even if he cannot see the SSID, so let say you are at a coffe shop, someone with the tools can figure out you are trying to connect to test SSID even if the test ssid is on your work place.
Wireless security consists of two main elements: authentication and encryption. Authentication controls access to the network and encryption ensures that malicious users cannot determine the contents of wireless data frames. Although having users manually configure the SSID of a wireless network in order to connect to it creates the illusion of providing an additional layer of security, it does not substitute for either authentication or encryption.
A non-broadcast network is not undetectable. Non-broadcast networks are advertised in the probe requests sent out by wireless clients and in the responses to the probe requests sent by wireless APs. Unlike broadcast networks, wireless clients running Windows XP with Service Pack 2 or Windows Server® 2003 with Service Pack 1 that are configured to connect to non-broadcast networks are constantly disclosing the SSID of those networks, even when those networks are not in range.
Therefore, using non-broadcast networks compromises the privacy of the wireless network configuration of a Windows XP or Windows Server 2003-based wireless client because it is periodically disclosing its set of preferred non-broadcast wireless networks. When non-broadcast networks are used to hide a vulnerable wireless network—such as one that uses open authentication and Wired Equivalent Privacy—a Windows XP or Windows Server 2003-based wireless client can inadvertently aid malicious users, who can detect the wireless network SSID from the wireless client that is attempting to connect. Software that can be downloaded for free from the Internet leverages these information disclosures and targets non-broadcast networks.
So at the end i dont think its a good idea to hide the SSID anymore after reading those articles.
Here are the sources
http://technet.microsoft.com/en-us/library/bb726942.aspx#EDAA
http://blogs.technet.com/b/steriley/archive/2007/10/16/myth-vs-reality-wireless-ssids.aspx
Any thoughs on this are welcome.
Cheers
Carlos