When you authenticate a user on an Aruba Controller with a radius server, you have the option of sending back an attribute that has either the role or the VLAN that a user will be in. The limitation used to be that you can only send back a single VLAN or role, which makes putting a user into a specific "pool" almost impossible. You can now (as of ArubaOS 6.3) send back an attribute that has the VLAN name or pool that the user should be in from the radius server, using the Aruba-Named-User-Vlan radius attribute. Sending that attribute back will send the VLAN name or the VLAN pool name via Radius VSA and the local Aruba controller will convert the name to either a single VLAN or VLAN pool, based on how it is defined at the local controller. Here is how it works:
You authenticate a user, and based on attributes like AD group membership, the radius server will send back to the controller the Aruba-Named-User-Vlan attribute which will have a Name. Each local controller will have that VLAN Name assigned to a single VLAN or a VLAN pool so a user will be put in to a VLAN or VLAN pool based on how the local controller has the VLAN name configured. At a small location on a controller, the VLAN name "Employee" might be attached to a single VLAN, and at a larger location's controller the VLAN name "Employee" might be configured as a pool of VLANs. Either way, you simplify your radius configuration and you can interpret it locally at each controller. Here is how you would configure your enforcement profile in ClearPass Policy Manager to send back that Attribute:
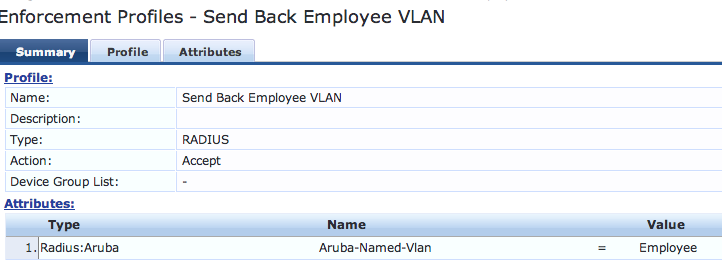
You would configure an enforcement policy that triggers the enforcement profile below to send back the "Employee" attribute below:

Here is how it looks in the Access Tracker on CPPM:

This is how it looks on the Aruba Controller. You first need to turn on authmgr logging to see radius attributes:
You turn on Authmgr logging by:
config t
logging level debugging security process authmgr
logging level debugging security subcat aaa
Then you type "show log security all" to see the following radius attributes sent back and fort
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:95] Radius authenticate raw using server cppm-192.168.1.32
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_request.c:52] Add Request: id=4, srv=192.168.1.32, fd=78
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1214] Sending radius request to cppm-192.168.1.32:192.168.1.32:1812 id:4,len:291
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] User-Name: employee
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] NAS-IP-Address: 192.168.1.3
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] NAS-Port-Id: 0
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] NAS-Identifier: 192.168.1.3
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] NAS-Port-Type: 19
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Calling-Station-Id: E892A4966F43
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Called-Station-Id: 000B866D2030
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Service-Type: Login-User
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Framed-MTU: 1100
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] EAP-Message: \002\004
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] State:
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Aruba-Essid-Name: ACME-TLS
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Aruba-Location-Id: ap-135
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Aruba-AP-Group: default
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Aruba-Device-Type: Android
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_server.c:1224] Message-Auth: \310\202\021\001G\244\336 \341\307\032\242\241{\373\266
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_request.c:76] Find Request: id=4, srv=192.168.1.32, fd=78
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_request.c:82] Current entry: srv=192.168.1.32, fd=78
May 19 13:50:25 :121038: <DBUG> |authmgr| Save Class in station for MAC e8:92:a4:96:6f:43.
May 19 13:50:25 :121040: <DBUG> |authmgr| rc_recv_server_async: last_authserver cppm-192.168.1.32.
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_request.c:37] Del Request: id=4, srv=192.168.1.32, fd=78
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1013] Authentication Successful
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1015] RADIUS RESPONSE ATTRIBUTES:
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] {Microsoft} MS-MPPE-Recv-Key: \307\277\374)\251\346\206}Jx\350y\363d\325\321@\233f\013l\3710\023\205\230A\017\300\333\002b\341\250\240\312\3778\226d\002\365\206\215\262>\376/uk
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] {Microsoft} MS-MPPE-Send-Key: \311}\261
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] EAP-Message: \003\004
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] Message-Auth: \234\312\376Z\243\362\320\221\371\004\022Q\252\007?y
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] User-Name: employee
May 19 13:50:25 :121031: <DBUG> |authmgr| |aaa| [rc_api.c:1030] {Aruba} Aruba-Named-User-Vlan: Employee
#AP325#AP-300