Question
How do you restrict ssh to only trusted hosts in CX?
Like "ip authorized-managers" in AOS-S/ProCurve, or "ip access-class" in Cisco.
Answer
Use Control Plane ACLs.
These have been available in CX since 10.2, and allow both IP and IPv6 hosts and networks to access the control plane.
You can find the relevant manual for your switch with this search:
ACLs and Classifier Policies Guide
Create the Access Control List (ACL)
This is broken into 3 sections:
- permit specific items (host or subnets) for designated port types
- block those specific port types for everything else
- override the implicit deny with an explicit allow (this is the catch-all to prevent inadvertently blocking important protocols or elements - like dhcp-relay)
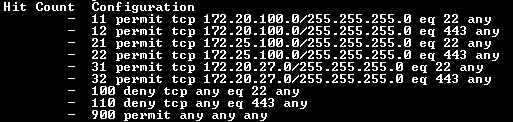
access-list ip authorized-managers
10 permit tcp 172.20.100.0/255.255.255.0 any eq 22
10 comment Allows BV-main access to switch
11 permit tcp 172.20.100.0/255.255.255.0 any eq 443
12 permit udp 172.20.100.0/255.255.255.0 any eq 161 count
20 permit tcp 172.25.100.0/255.255.255.0 any eq 22
20 comment Allows WGA-main access to switch
21 permit tcp 172.25.100.0/255.255.255.0 any eq 443
30 permit tcp 172.20.27.0/255.255.255.0 any eq 22
30 comment Allows BVsubnet27 access to switch
31 permit tcp 172.20.27.0/255.255.255.0 any eq 443
100 deny tcp any any eq 22 count
100 comment block key management protocols from any other subnet
101 deny tcp any any eq 443 count
102 deny udp any any eq 161 count
103 deny tcp any any eq 80 count
200 permit any any any count
200 comment allow everything else
Apply the ACL
apply access-list ip authorized-managers control-plane vrf default
Counters
Counters help to identify what rules are permitting or denying traffic; they are enabled per rule (ACE).
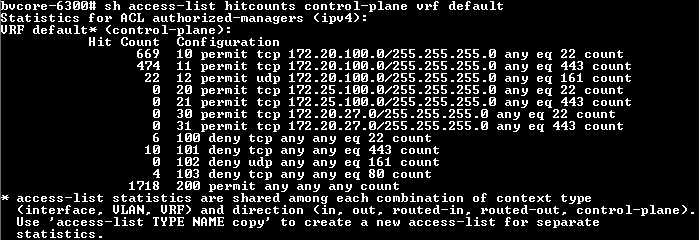
I was able to successfully block access from SSH, HTTP/HTTPS (and later SNMP, although that is not shown in the count here).
Note the 1718 hits for other things. That will include NTP. I also had issues with DHCP-relay before I reorganised it as described.
If you don't include the "count" parameter in an access-list, nothing will be displayed: