Can you try to check on the AP itself, for example with Console Session from Central or direct SSH or serial console into the AP, if the certificate is actually updated and active? If you have a CLI session, you can run the command: "show cert" to see which certificates are present for which features.
I was not aware of the possibility to add a custom RadSec client certificate, so it may also be new to recent firmware. I would expect a message indicating incompatibility, but let's start to see if the configuration has been pushed correctly.
If it is there, but also if it is not there, you can open a case with support either on the certificate not being pushed from Central, or the pushed certificate not being used.
------------------------------
Herman Robers
------------------------
If you have urgent issues, always contact your Aruba partner, distributor, or Aruba TAC Support. Check
https://www.arubanetworks.com/support-services/contact-support/ for how to contact Aruba TAC. Any opinions expressed here are solely my own and not necessarily that of Hewlett Packard Enterprise or Aruba Networks.
------------------------------
Original Message:
Sent: Feb 01, 2021 10:18 AM
From: Alexander Shulgin
Subject: RadSec ignores custom certificate
Thank you for the root certificate I will try to use it shortly.
RadSec uses mutual certificate authentication...
I understand that, and this is why I have uploaded my own certificate
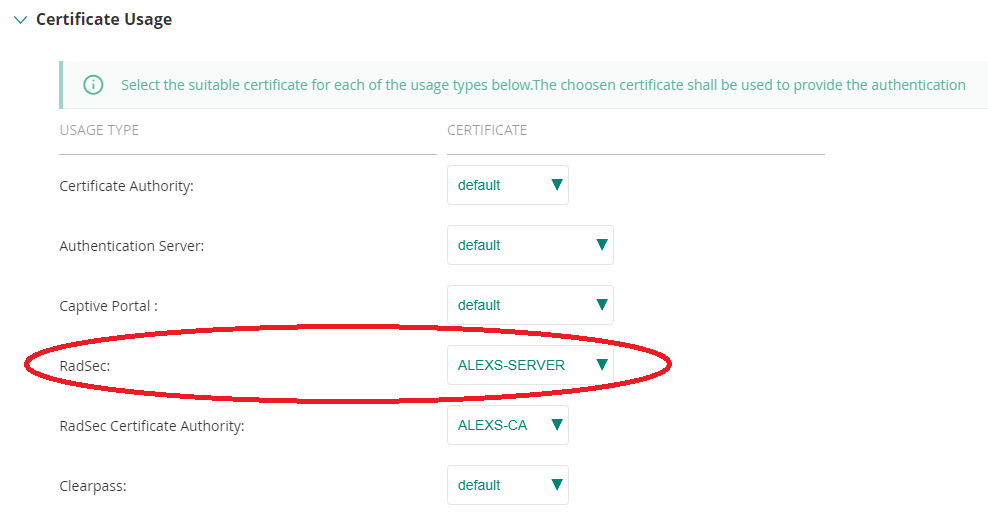
And my expectation was that AP should use it rather than continue to use the Aruba's default.
By putting that root certificate on RadSecProxy side it will open the TLS authentication to all Aruba access points. But i want to restrict it only to these who are using my certificate.
Thanks.
------------------------------
Alexander Shulgin
Original Message:
Sent: Feb 01, 2021 05:36 AM
From: Herman Robers
Subject: RadSec ignores custom certificate
RadSec uses mutual certificate authentication and the message you see indicates that your RADIUS server is no accepting/trusting the certificate used by the AP (RadSec client): tls_process_client_certificate:certificate verify failed
I attached the RootCA, that I pulled from ClearPass that has it built-in, but other RADIUS server don't. The file is in a zip as it didn't allow me to upload otherwise, so extract first. You will need to add this and configure your radsecproxy to trust this certificate for incoming RADIUS clients.
------------------------------
Herman Robers
------------------------
If you have urgent issues, always contact your Aruba partner, distributor, or Aruba TAC Support. Check https://www.arubanetworks.com/support-services/contact-support/ for how to contact Aruba TAC. Any opinions expressed here are solely my own and not necessarily that of Hewlett Packard Enterprise or Aruba Networks.
Original Message:
Sent: Jan 29, 2021 01:40 PM
From: Alexander Shulgin
Subject: RadSec ignores custom certificate
Hello everybody,
I need some technical advice from experts here.
I am trying to configure RadSec tunnel between my group in Aruba Central and radsecproxy.
To do this I generated selfsigned certificates for CA, Server and client by following the instruction provided for FreeRadius
https://github.com/FreeRADIUS/freeradius-server/tree/v3.0.x/raddb/certs
In radsecprocy config file I updated the certification section to use my custom CA and server certificate.
On Aruba Central I uploaded CA (as CA Certificate) and Client Certificate (as Server Certificate)
Then in my Group->Security->Certificate Usage section I changed the "RadSec Certificate Authority" to be my CA, and
"RadSec" to be my Client certificate.
Now, when AP connects to radsecproxy I see that it accepts my server certificate (means CA certificate works fine), but then radsecproxy rejects the connection saying
Jan 29 11:35:11 2021: tlsservernew: incoming TLS connection from 192.168.82.127
Jan 29 11:35:11 2021: verify error: num=20:unable to get local issuer certificate:depth=2:/C=US/O=Aruba Networks/OU=DeviceTrust/OU=Operations/CN=Aruba Networks Trusted Computing Policy CA 2.0
Jan 29 11:35:11 2021: tlsservernew: SSL accept from 0.0.0.0/0 failed: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Jan 29 11:35:11 2021: tlsservernew: SSL_accept failed
I think, based on what it printing about the issuer, the Aruba Central is still using the "default" certificate ignoring the uploaded one.
What I am doing wrong? Any suggestions?
Thanks.
------------------------------
Alexander Shulgin
------------------------------