Good day!
AOS-CX Downloadable User Role (DUR) simple steps to Configure!
Prior condition or prerequisite:
Note 1: DUR is Aruba solution, means it works with Aruba Clearpass Radius-Server.
Note 2: Simple DUR CX Switch required configuration is attached at the end. Step by Step process is below:
Step1: Configuring/Installing TA-Certificate on CX switches.
Example of installing ta-certificate.
BLDG02-F1(config)#crypto pki ta-profile cp
ta-certificate
-----BEGIN CERTIFICATE-----
MIIDYzCCAkugAwIBAgIQZiDAdPhWQqNE3PpMDBcTBjANBgkqhkiG9w0BAQsFADBE
MRMwEQYKCZImiZPyLGQBGRYDbmV0MRYwFAYKCZImiZPyLGQBGRYGdG1lbGFiMRUw
EwYDVQQDEwx0bWVsYWItQUQtQ0EwHhcNMTcwMzI5MDExMzA4WhcNMjIwMzI5MDEy
MzA4WjBEMRMwEQYKCZImiZPyLGQBGRYDbmV0MRYwFAYKCZImiZPyLGQBGRYGdG1l
bGFiMRUwEwYDVQQDEwx0bWVsYWItQUQtQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IB
DwAwggEKAoIBAQDrdqdR2QQm4Lo3i/X9bvTu41cf3sVFzPFn727zlgrYySXWtyvW
M3Jzf6P3FsqQzrsaP+QhlNsYMTrY2Yiccm7C9gNshpx95elzXsZ2TBP88qoUPD9F
jH42YgnqAN61+opmct8aRgSJhTtKv+WEolVtLgL9/CL3zmvmbpz3oyYjF9W3lesp
D52BeEbPqsBrALbYQypxJJLonZuueM7ePhSYbPnbrGuV8M9BiDyEyQ87OUYGgq7J
krwjrer+BKYFIxqJQDHbY96ozbaUScv8nOylpUrH56r3jT5Xn05JDdOIJvBKniYK
ZxIK+m4Mv2XS0zxuZBG1F1YDl/bcQ353jazbAgMBAAGjUTBPMAsGA1UdDwQEAwIB
hjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQuBjOz0LpCALxkgy9bWbziV+1D
UDAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOCAQEAydVR86YZez9N
uIvJOftLczu0y3YfGoA5PK88Yv3TSMv+gxK5yiceU2HkV3PvVeCXyN9Nn9EUKLJ8
87/BqDTsNKKD20axHNk/w2p5I8LY6g/Y8t3N84gXx3439+GezBdlxznEmWAhebAQ
/JMnp+aD9Xhw9tgGeDXMB/GIhx0PCK22VbRUoDeZP3o+LmdB2fOdqhfN8+e2OMpz
AGsBGGEJJWqOKSUkHC25Jkl0RfyymdxuWEflHofbF2DjSWheR023A5dA6a5WkxTV
7WxwC8ekitnlY5BT2ZHV1LXLUsgvuN3j8G2+yvYiS6Z/da3ORb6Grm79sqZpzlKZ
XWjU/zVxBQ==
-----END CERTIFICATE-----
END_OF_CERTIFICATE
BLDG02-F1# show crypto pki ta-profile
TA Profile Name TA Certificate Revocation Check
-------------------------------- -------------------- ----------------
cp Installed, valid disabled
BLDG02-F1#
!#Use below command to see certificate validity and more details:
BLDG02-F1# show crypto pki ta-profile cp
!#no role is configured on CX switch
BLDG02-F1# show running-config port-access
BLDG02-F1#
If you have questions regarding how to generate these certificate, please leave your comments, will cover in next write up.
Step2: Radius-server configuration
Please refer to below post and configure Radius server.
https://community.arubanetworks.com/t5/Wired-Intelligent-Edge-Campus/AOS-CX-Radius-server-simple-steps-to-Configure/m-p/663009#M10219
BLDG02-F1# sh radius-server
Unreachable servers are preceded by *
******* Global RADIUS Configuration *******
Shared-Secret: None
Timeout: 5
Auth-Type: pap
Retries: 1
TLS Timeout: 5
Tracking Time Interval (seconds): 60
Tracking Retries: 5
Tracking User-name: radius-tracking-user
Tracking Password: None
Number of Servers: 1
-------------------------------------------------------------------------------------------------
SERVER NAME | TLS | PORT | VRF
-------------------------------------------------------------------------------------------------
aoss-cppm.tmelab.net | | 1812 | mgmt
-------------------------------------------------------------------------------------------------
BLDG02-F1#
BLDG02-F1# ping aoss-cppm.tmelab.net vrf mgmt repetitions 1
PING aoss-cppm.tmelab.net (10.5.8.12) 100(128) bytes of data.
108 bytes from 10.5.8.12: icmp_seq=1 ttl=61 time=0.545 ms
--- aoss-cppm.tmelab.net ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.545/0.545/0.545/0.000 ms
BLDG02-F1#
Step3: Make sure Client is connected to CX switch
BLDG02-F1# sh mac-address-table port
PORTS List of Ports [e.g. 1/1/1 or 1/1/1-1/1/3 or lag1]
BLDG02-F1# sh mac-address-table port 1/1/5
MAC age-time : 300 seconds
Number of MAC addresses : 1
MAC Address VLAN Type Port
--------------------------------------------------------------
2c:41:38:7f:27:05 1 dynamic 1/1/5
BLDG02-F1#
BLDG02-F1# sh running-config interface 1/1/5
interface 1/1/5
no shutdown
vlan access 1
exit
BLDG02-F1#
Step4: Configure 802.1x or mac-auth on client connected interface
!# Enable on global mode and then on connected interface as below.
BLDG02-F1(config)# aaa authentication port-access mac-auth enable
BLDG02-F1(config-if)# aaa authentication port-access mac-auth enable
BLDG02-F1# sh running-config interface 1/1/5
interface 1/1/5
no shutdown
vlan access 1
aaa authentication port-access mac-auth
enable
exit
BLDG02-F1#
Step4: Configure Profile, Policies and Service on Clearpass.
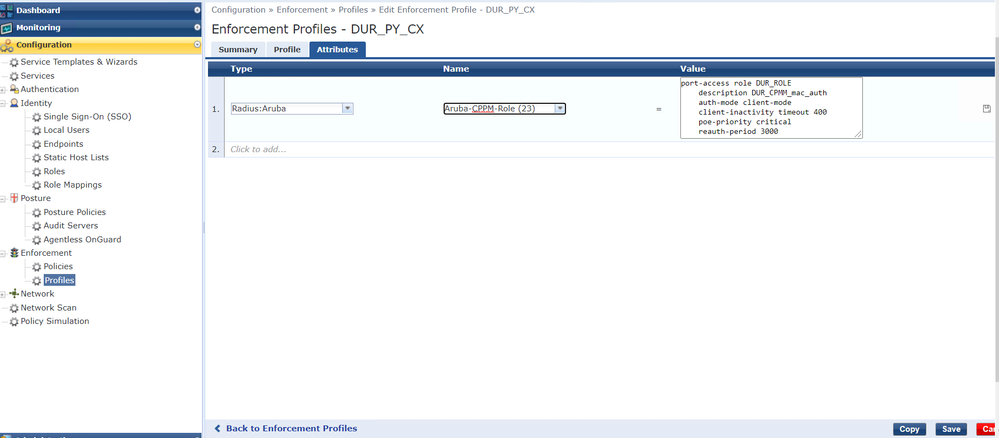
Note that every configuration should be exactly same as local role
Let's add this profile to policies in clearpass.
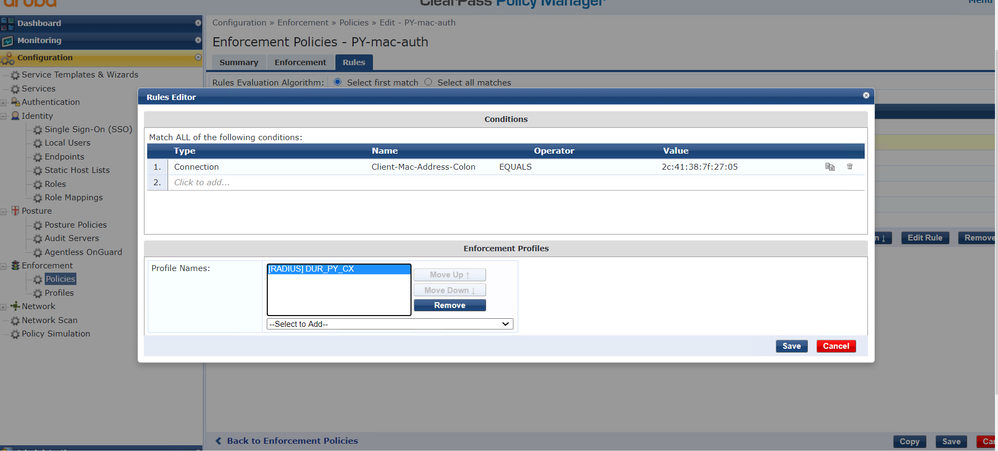
Let's add this policies into a service
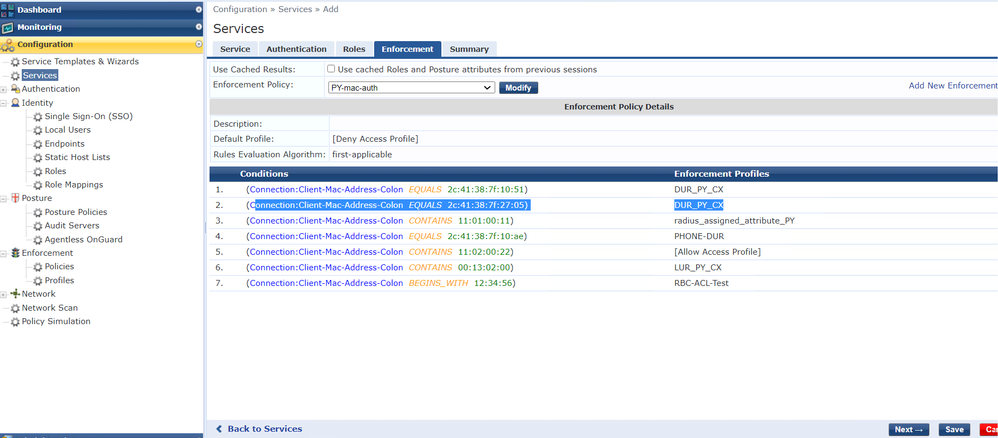
Let's Validate:
BLDG02-F1# show port-access clients detail
Port Access Client Status Details:
Client 2c:41:38:7f:27:05, 2c41387f2705
============================
Session Details
---------------
Port : 1/1/5
Session Time : 918s
IPv4 Address :
IPv6 Address :
Authentication Details
----------------------
Status : mac-auth Authenticated
Auth Precedence : dot1x - Not attempted, mac-auth - Authenticated
Authorization Details
----------------------
Role : DUR_PY_CX-3099-2
Status : Applied
Role Information:
Name : DUR_PY_CX-3099-2
Type : clearpass
Status: Completed
----------------------------------------------
Reauthentication Period : 3000 secs
Authentication Mode : client-mode
Session Timeout :
Client Inactivity Timeout : 400 secs
Description : DUR_CPMM_mac_auth
Gateway Zone :
UBT Gateway Role :
Access VLAN :
Native VLAN :
Allowed Trunk VLANs :
Access VLAN Name :
Native VLAN Name :
Allowed Trunk VLAN Names :
MTU :
QOS Trust Mode :
STP Administrative Edge Port :
PoE Priority : critical
Captive Portal Profile :
Policy :
BLDG02-F1#
BLDG02-F1# sh aaa authentication port-access interface all client-status
Port Access Client Status Details
Client 2c:41:38:7f:27:05, 2c41387f2705
============================
Session Details
---------------
Port : 1/1/5
Session Time : 1060s
IPv4 Address :
IPv6 Address :
Authentication Details
----------------------
Status : mac-auth Authenticated
Auth Precedence : dot1x - Not attempted, mac-auth - Authenticated
Authorization Details
----------------------
Role : DUR_PY_CX-3099-2
Status : Applied
BLDG02-F1#
BLDG02-F1# sh port-access clients
Port Access Clients
--------------------------------------------------------------------------------
Port MAC Address Onboarded Status Role
Method
--------------------------------------------------------------------------------
1/1/5 2c:41:38:7f:27:05 mac-auth Success DUR_PY_CX-3099-2
BLDG02-F1#
Thank you,
Yash