If you have urgent issues, always contact your Aruba partner, distributor, or Aruba TAC Support. Check
for how to contact Aruba TAC. Any opinions expressed here are solely my own and not necessarily that of Hewlett Packard Enterprise or Aruba Networks.
In case your problem is solved, please invest the time to post a follow-up with the information on how you solved it. Others can benefit from that.
Original Message:
Sent: Jun 30, 2023 03:37 AM
From: KrisVe
Subject: Cert-based Wireless Auth using User AND Machine Certs?
I've noticed that the problem doesn't occur if the service only has TEAP as authentication method, not TEAP and TLS together (which it had during the migration from TLS to TEAP via GPO). Changing the order of the authentication methods on the one service didn't matter.
Kris
Original Message:
Sent: Jun 26, 2023 11:15 AM
From: Herman Robers
Subject: Cert-based Wireless Auth using User AND Machine Certs?
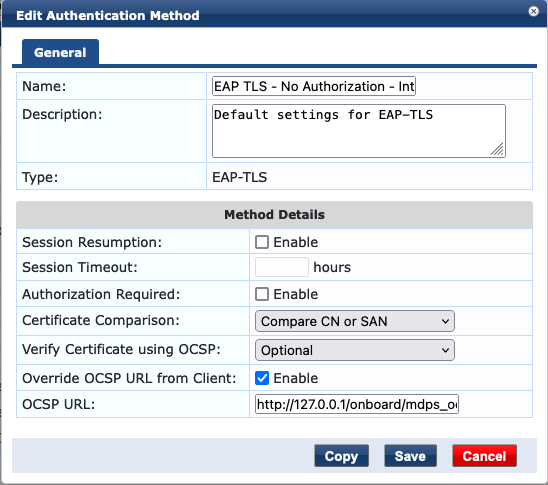
The error seems related to the Compare Certificates option in the EAP-TLS method (used the TEAP method). You can try to set to to 'Compare CN or SAN' or temporarily do not compare to verify that the issue lies in the cert comparison:
------------------------------
Herman Robers
------------------------
If you have urgent issues, always contact your Aruba partner, distributor, or Aruba TAC Support. Check https://www.arubanetworks.com/support-services/contact-support/ for how to contact Aruba TAC. Any opinions expressed here are solely my own and not necessarily that of Hewlett Packard Enterprise or Aruba Networks.
In case your problem is solved, please invest the time to post a follow-up with the information on how you solved it. Others can benefit from that.
Original Message:
Sent: Jun 22, 2023 05:13 AM
From: KrisVe
Subject: Cert-based Wireless Auth using User AND Machine Certs?
@zshore have you been able to resolve this? I'm facing the same issue, with a twist: for wired connections (TEAP, computer & user auth) it works perfectly, for wireless it fails with this message:
eap-teap: Method 1 failed for transaction
eap-teap: Method 1 failed for transaction
eap-teap: Conflicting identities 'anonymous' and 'host/SVCKVVS-2305.domain.local' in the request
TLS session reuse error
I'm using the same certificates (from our enterprise CA) for wired and wireless
Thx,
Kris
Original Message:
Sent: Feb 21, 2023 01:07 PM
From: zshore
Subject: Cert-based Wireless Auth using User AND Machine Certs?
I followed the instructions. But to no luck. Getting:
eap-teap: Method 1 failed for transaction
eap-teap: Method 1 failed for transaction
eap-teap: Conflicting identities 'anonymous' and 'host/Sectigo RSA Domain Validation Secure Server CA' in the request
TLS session reuse error
Original Message:
Sent: Jan 26, 2023 12:09 PM
From: Herman Robers
Subject: Cert-based Wireless Auth using User AND Machine Certs?
+1 on that. One benefit of TEAP is that the User Authentication can fail if the computer authentication succeeded, but you can still provide access to the network and that allows the client to retrieve the user certificate. Check here for a video on TEAP, this is with AD/GPO issued certificates, but works similar with Intune controlled certificates.
------------------------------
Herman Robers
------------------------
If you have urgent issues, always contact your Aruba partner, distributor, or Aruba TAC Support. Check https://www.arubanetworks.com/support-services/contact-support/ for how to contact Aruba TAC. Any opinions expressed here are solely my own and not necessarily that of Hewlett Packard Enterprise or Aruba Networks.
In case your problem is solved, please invest the time to post a follow-up with the information on how you solved it. Others can benefit from that.
Original Message:
Sent: Jan 26, 2023 07:45 AM
From: ahollifield
Subject: Cert-based Wireless Auth using User AND Machine Certs?
Use TEAP. Inner method EAP-TLS for each, machine certificate for the first chain, user certificate for the second.
Original Message:
Sent: Jan 26, 2023 03:05 AM
From: zshore
Subject: Cert-based Wireless Auth using User AND Machine Certs?
We have Clearpass deployed using the InTune connector. (Not the newest version of the connector). Then we use ScepMan to deploy USER and MACHINE certs.
I know some people say to either pick user or just machine if you have some shared devices, but we do some VLAN moving depending on who is logging into the device.
So today we get a new laptop in. It is imaged on site and provisioned in InTune and gets all our Scep and Wifi policy. It successfully joins the wi-fi network on the lockscreen with the machine cert. Then I go to log in with my creds and it does allow me to login, but the autoconnection to the wifi with the user cert does not happen because the cert does not get onto the device in time.
- Is there anyone else out there that uses both machine and user certs that has gotten around this?
- Is there a way to hold onto the machine authentication just a little longer after I login to be able to reach out and grab that cert in enough time? Anything regarding Authentication period, Authentication retry delay period, Start period, Maximum EAPOL-start, Maximum authentication failures?
I thought maybe if I increased the auth period to a minute or two, that could solve the issue?
I have verified with Scepman support that my config is good on the cert profile side, but this is definetily something I want to tweak in InTune for the wifi profile side.