Introduction- This article explains how to authenticate Cisco admin user against CPPM.
Environment-
Applicable to all the ClearPass versions.
Tested Cisco Platform.
- Cisco 4400 Wireless LAN Controller running 7.0.216.0
The Cisco configuration described in this article is applicable from 4.0.206.0 and later release.
Please find below the network configuration example parameters.
- Cisco WLC IP address – 10.130.226.85
- CPPM Server IP address– 10.130.226.53
Configuration Steps- The below steps will walk you through with the configuration on CPPM and Cisco WLC.
Step 1: Adding CPPM as RADIUS server in Cisco WLC.
From the Cisco WLC GUI, navigate to Security >> AAA >> Radius >> Authentication >> New >> and add the CPPM server IP address and the shared-secret key.
Note:
- The Radius server that we are going to configure will be used for MANAGEMENT authentication, so enable the Management check box in the same configuration page to allow the CPPM to manage the users.
- The shared-secret key should be same on CPPM and Cisco WLC.

Step 2: Adding Cisco WLC as Network/NAS device in CPPM.
From the CPPM GUI, navigate to Configuration >> Network >> Devices and Add the Cisco WLC as shown below.

Step 3: Creating Enforcement Profiles.
Cisco WLC supports 3 modes of user permissions, read-write, read-only and lobby administrator.
- For read-write permission you need to return Radius:IETF Service-Type attribute with the value Administrative.
- For read-only permission return the Service-Type with value NAS-Prompt
- For lobby administrator return the Service-Type value Callback-Administrative
In the below examples, you will be seeing the Enforcement profiles for read-write and read-only users.
From CPPM GUI, navigate to Configuration >> Enforcement Profiles >> Add and Create RADIUS Based Enforcement and map the RADIUS:IETF Service-Type attribute with the corresponding values as shown below.


Named the above enforcement profiles as Cisco-administrative and Cisco-Read only.
Step 4: Creating Enforcement policy.
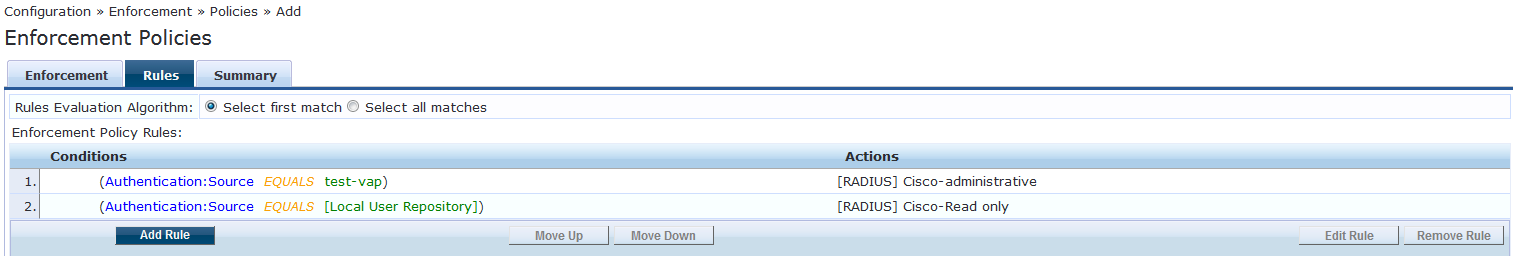
In the below example, we are assigning read-write permission for the user from (AD)Active Directory and read-only permission for the user from [Local User Repository]. The below enforcement policies is just an example, please create the enforcement policies/conditions based on your requirement.
The sample Active Directory used in this test is "test-vap", which had already be created under Configuration >> Authentication >> Sources.
Navigate to Configuration >> Enforcement >> Policies.
Step 5: Creating a service.
Navigate to Configuration >> Services and create a Radius Enforcement(Generic) service. You could restrict the service rule with the Cisco WLC IP address for service categorization(Please refer the below screen capture for sample service rule configuration).

Mapping Authentication Method and Sources to the service.

Mapping the created enforcement policy to the service.

Answer-Please refer the below screen captures, showing WLC login against CPPM using the AD account and the access tracker output followed by successful authentication.

