Requirement:
This article is about creating enforcement policy to check the users based on their certificate expiration time and send them to a different role (BYOD role) to re-provision their device. Also send alert email to notify the administrator and the user about the certificate expiration.
Solution:
- We can use access tracker computed attributes to check the certificate validity and send the user to a different role (BYOD role) to re-provision their device.
- Using this method we can stop the user getting rejected/blocked due to certificate expires.
Note: This article is mainly focused on enforcement policy to check the validity and send the BYOD role. Please visit the link below for ClearPass OnBoard integration or search our community for implementation queries.
https://support.arubanetworks.com/Documentation/tabid/77/DMXModule/512/EntryId/33093/Default.aspx
Configuration:SMTP configuration:
1. Configure email gateway in Policy Manager under Administration >> External Servers >> Messaging Setup.
2. Configure SMTP settings and validate using the "Send Test Email" option.

Create API Client ID:
1. Navigate to Guest >> Administration >> API Services >> API Clients >> Create API client
2. Copy "Client ID" and "Client secret" to use it in the endpoint context server configuration.

Endpoint Context Server Configuration:
1. Navigate to ClearPass Policy Manager >> Administration >> External Servers >> Endpoint Context Servers and select "localhost".
Note: If the Endpoint Context Server "localhost" is already in use, then it is recommended to create a new context server and follow the below sample configuration.
2. Select Authentication Method as "OAuth2", enter client id and secret.
3. Use "Validate" option to check if the connection is working.

Creating Context Server Actions:
1. Navigate to ClearPass Policy Manager >> Administration >> Dictionaries >> Context Server Actions >> Add
2. Under Action, select Server Type: Generic HTTP, Server Name: localhost, Action Name, HTTP Method: POST, Authentication Method: None and URL: /api/email/send

3. Enter the below Header Names.

4. Enter the below JSON attributes in the Content field:
Content-Type: JSON
Content:
{
"to": ["%{Certificate:Subject-AltName-Email}"],
"subject": "Your network access is about to expire",
"message": "The certificate used by your %{Endpoint:Device Type} device %{Endpoint:Product Name} to access the network will expire at %{Certificate:Not-Valid-After}",
"headers": {"Content-Type":"text/plain; charset=UTF-8"}
}

Note: Modify the To, Subject and messages based on the requirement.
Model Schema for Content:
{
to (object, optional): List of Recipients Email Address (e.g., ["a@example.com", "b@example.com"]),
subject (string, optional): Email Subject,
message (string, optional): Email Body,
cc_recipients (object, optional): List of CC recipients Email Address (e.g., ["a@example.com", "b@example.com"]),
bcc_recipients (object, optional): List of BCC recipients Email Address (e.g., ["a@example.com", "b@example.com"]),
headers (object, optional): Email headers (e.g., {"Content-Type":"text/plain; charset=UTF-8","Content-Transfer-Encoding": "8bit"})
}
Service Configuration:
1. To create enforcement profile, navigate to Configuration >> Enforcement >> Profile >> Add >> HTTP Based Enforcement
2. Select Endpoint Context server and Context server action.

3. In the provisioning service (802.1x), we can add the below enforcement policy rule to check the certificate validity.
(Authentication EQUALS EAP-TLS)
AND (AuthorizationTime SourceOne Week DT GREATER_THAN_OR_EQUALS %CertificateNot-Valid-After})
- User will hit this condition if the certificate expires in less than one week.
- The user will be sent to the pre-provisioning role to re-onboard their device to get a new certificate and also "API SMTP Profile" to trigger email.

VerificationUsers should be able to re-onboard the device when the clients are assigned with BYOD/pre-provision role, assigned role can be confirmed from ClearPass Access Tracker and on the NAS (controller/switch).
The email alert sent will be logged in the Application logs, under ClearPass Guest > Administration > Support > Application Log.

Sample Email alert:
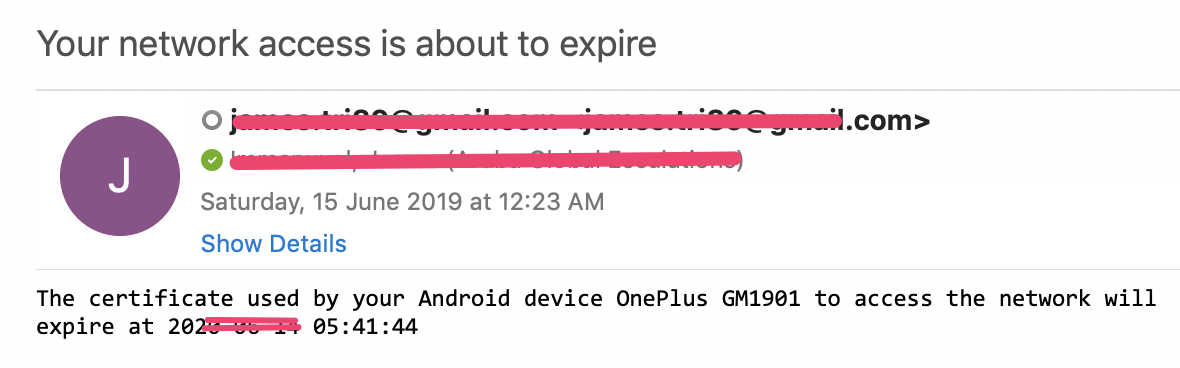
Attachment:
Enforcement profile attached. We can restore this in Configuration > Enforcement > Profiles > Import.
It will restore the below configuration:
- Enforcement Profile: API SMTP Profile
- Endpoint Context Servers: localhost
- Context Server Actions: API SMTP
Note: Update Endpoint context server with correct oauth2 credentials.
Attachments:API_SMTP_Enforcement_OnBoard.xml