Question: How does role derivation work with different combinations of MAC Auth Fail-Thru & Enforce MAC Auth Only Role options?
Environment:Aruba Instant running 6.2.1.0-3.3.0.0 or above with MAC + 802.1x wired authentication enabled
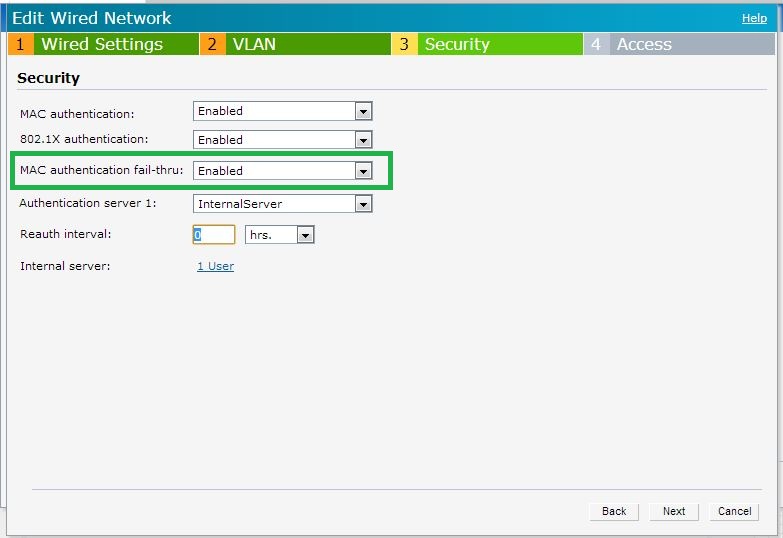
MAC Auth Fail-Thru
With MAC & 802.1x authentication configured; MAC authentication occurs first. By default; 802.1x authentication wouldn't be attempted for a client which fails MAC authentication. However; MAC authentication fail-thru (CLI Command :: l2-auth-failthrough) allows a client to attempt 802.1x authentication even when it fails MAC authentication.
Enforce MAC Auth Only Role
Enforce MAC auth only role (CLI Command :: set-role-mac-auth ) allows to assign a unique role for a client which passes MAC auth but fails 802.1x authentication.
Below are four possible scenarios with the above two option configuration and corresponding expected role assignment.

Scenario I ::
| MAC authentication fail-thru |
Enforce MAC auth only role |
| Disabled |
Disabled |
Sample CLI Wired Profile Configuration :
wired-port-profile wired-user
switchport-mode access
allowed-vlan all
native-vlan 1
no shutdown
access-rule-name wired-user
speed auto
duplex auto
poe
type employee
auth-server InternalServer
captive-portal disable
mac-authentication
dot1x
Role Assignment :
| MAC Auth |
Dot1x |
Role Assignment |
| Fail |
Doesn’t Occur |
DenyAll |
| Pass |
Fail |
DenyAll |
| Pass |
Pass |
Default / Derived Role |
Scenario II ::
| MAC authentication fail-thru |
Enforce MAC auth only role |
| Disabled |
Enabled |
Sample CLI Wired Profile Configuration :
wired-port-profile wired-user
switchport-mode access
allowed-vlan all
native-vlan 1
no shutdown
access-rule-name wired-user
speed auto
duplex auto
poe
type employee
auth-server InternalServer
captive-portal disable
mac-authentication
dot1x
set-role-mac-auth <role name>
Role Assignment :
| MAC Auth |
Dot1x |
Role Assignment |
| Fail |
Doesn’t Occur |
DenyAll |
| Pass |
Fail |
MAC Auth Only Role |
| Pass |
Pass |
Default / Derived Role |
Scenario III ::
| MAC authentication fail-thru |
Enforce MAC auth only role |
| Enabled |
Disabled |
Sample CLI Wired Profile Configuration :
wired-port-profile wired-user
switchport-mode access
allowed-vlan all
native-vlan 1
no shutdown
access-rule-name wired-user
speed auto
duplex auto
poe
type employee
auth-server InternalServer
captive-portal disable
mac-authentication
l2-auth-failthrough
dot1x
Role Assignment :
| MAC Auth |
Dot1x |
Role Assignment |
| Fail |
Fail |
DenyAll |
| Fail |
Pass |
Default / Derived Role |
| Pass |
Fail |
DenyAll |
| Pass |
Pass |
Default / Derived Role |
Scenario IV ::
| MAC authentication fail-thru |
Enforce MAC auth only role |
| Enabled |
Enabled |
Sample CLI Wired Profile Configuration :
wired-port-profile wired-user
switchport-mode access
allowed-vlan all
native-vlan 1
no shutdown
access-rule-name wired-user
speed auto
duplex auto
poe
type employee
auth-server InternalServer
captive-portal disable
mac-authentication
l2-auth-failthrough
dot1x
set-role-mac-auth <role name>
| MAC Auth |
Dot1x |
Role Assignment |
| Fail |
Fail |
DenyAll |
| Fail |
Pass |
Default / Derived Role |
| Pass |
Fail |
MAC Auth Only Role |
| Pass |
Pass |
Default / Derived Role |