Environment :
Any Aruba Instant AP
Aruba Instant 6.2.1.0-3.3.x.x
Clear Pass Policy Manager
Android clients can connect back to the 802.1x SSID although we have revoked the client credentials from CPPM.
IOS clients will not be able to connect back and denied when they try to do full authentication.
It could be due to PMK Cache that can allow clients to reconnect to an AP after they have roamed to another AP and come back, or Auth-survivability if CPPM is used along with IAPs
This issue can occur for employees that are no longer in service and we remove/revoke their authentication credentials from the Radius Server (CPPM). However, we may notice non-IOS clients are still able to get on to the network immediately after revoking credentials. This is because IOS devices don't support key-caching features like OKC.
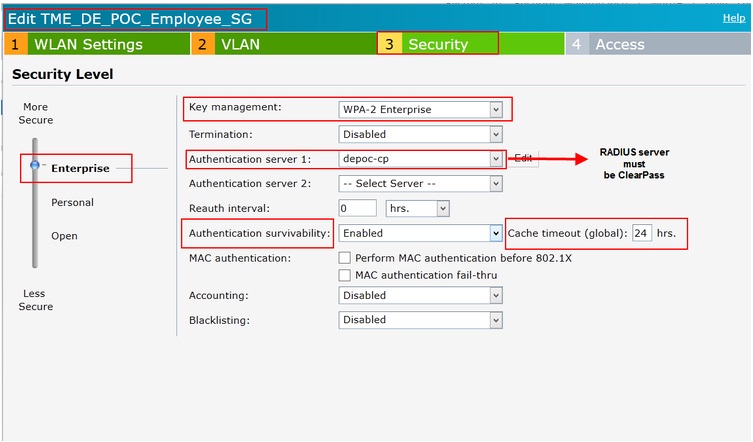
As of this writing, IAPs don’t yet support OKC, however PMK Cache is supported and could be a feature but options are limited and we cannot change the PMK Cache timer. This issue can also be caused by one other similar feature to PMK Caching but it’s a different feature altogether, is “Authentication Survivability”. If the customer has this enabled, we need to modify the timer or disable it to make users re-authenticate when connecting to the 802.1x SSID.
As a comparison for a similar scenario with Aruba Controllers, here are our options:
1) This could be due to PMK Cache, that allows the Controller to remember the PMKID (defaults to 8 hours). This cache timer can be reduced upto 1 hour:
Example:
(Aruba) (config) #aaa authentication dot1x default
(Aruba) (802.1X Authentication Profile "default") #timer keycache-tmout 1
(Aruba) (802.1X Authentication Profile "default") #write mem
2) If we intend to remove clients from the network or revoke their credentials then we may blacklist users until the cache times out i.e.:
(Aruba) (config) #ap ap-blacklist-time 3600
(Aruba) (config) #exit
(Aruba) #stm add-blacklist-client <client-mac>
(Aruba) (config) #write mem
3) Use WPA-TKIP if we can do without PMK Caching altogether.
This issue can occur for employees that are no longer in service and we remove/revoke their authentication credentials from the Radius Server (CPPM). However, we may notice non-IOS clients are still able to get on to the network immediately after revoking credentials. This is because IOS devices don't support key-caching features like OKC.
As of this writing, IAPs don’t yet support OKC, however PMK Cache is supported and could be a feature but options are limited and we cannot change the PMK Cache timer. This issue can also be caused by one other similar feature to PMK Caching but it’s a different feature altogether, is “Authentication Survivability”. If the customer has this enabled, we need to modify the timer or disable it to make users re-authenticate when connecting to the 802.1x SSID.
As a comparison for a similar scenario with Aruba Controllers, here are our options:
1) This could be due to PMK Cache, that allows the Controller to remember the PMKID (defaults to 8 hours). This cache timer can be reduced upto 1 hour:
Example:
(Aruba) (config) #aaa authentication dot1x default
(Aruba) (802.1X Authentication Profile "default") #timer keycache-tmout 1
(Aruba) (802.1X Authentication Profile "default") #write mem
2) If we intend to remove clients from the network or revoke their credentials then we may blacklist users until the cache times out i.e.:
(Aruba) (config) #ap ap-blacklist-time 3600
(Aruba) (config) #exit
(Aruba) #stm add-blacklist-client <client-mac>
(Aruba) (config) #write mem
3) Use WPA-TKIP if we can do without PMK Caching altogether.