This is a tutorial about how to manually generate TLS certificates from the ClearPass Onboard CA for Linux Clients, since Onboard does not have an automatic facility to do so for Linux devices. This tutorial assumes that you have already created your Onboard CA and Onboard is also distributing certificates automatically for other Client OSs. It also assumes that you already have a service in ClearPass Policy Manager created that will successfully authenticate clients that have EAP-TLS certificates generated by Onboard. It DOES NOT describe how to install the certificates on the many different flavors of Linux. Please consult directions on your Linux supplicant on how to install EAP-TLS certificates.
Steps:
1. On the main page of ClearPass policy manager, click on On ClearPass Onboard:
2. Go to Management and Control> View by Certificate
3. Click on "Generate A New Certificate Signing Request"

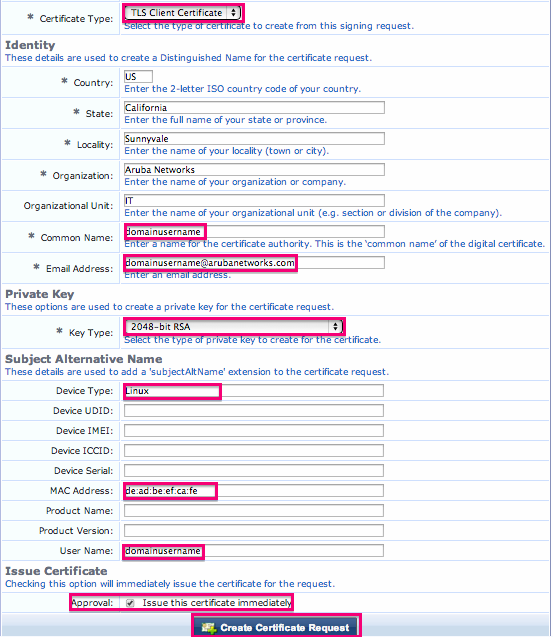
4. Ensure that
- The Certificate type is TLS Client Certificate
- The Common Name field matches the user's username in Active Directory of whatever directory you are using. This is so that you can later check to see if the account is active in that directory prior to successful authentication. It will also show up in the controller as the username of the certificate
- The email address field is filled out. This can be used in later versions of ClearPass to email the user when the certificate is about to expire.
- The Key Type is 2048-bit RSA
- The device type is Linux so that you will be able to know just by looking at the certificate in a List
- The Mac address field is filled out correctly. During authentication, you can optionally use this attribute to compare the mac address on the certificate with the mac address of the user as an additional check to make sure it was not copied.
- The username field matches the username
- Issue this certificate Immediately is checked
5. Find the certificate you just generated and click on Export Certificate.

6. Export the certificate in PKCS#12 format (.p12 extension) and put a strong passphrase on it. The passphrase will be used to install the client certificate later. Only the administrator should know this passphrase so that it can only be installed by the administrator and NOT the user. This is so that the user cannot install it on any other machine:

7. Save the .p12 file somewhere temporary:

8. Exporting the Server Certificate. On the ClearPass Policy Manager side, go to Administration> Certificates> Server Certificate:
9. Click on Export Server Certificate:

10. This will create a .zip file with a .crt file and a .pkey file. Destroy the .pkey file. You will only need the .crt server certificate file and .p12 file to install on the client. You will also need the the client's TLS passphrase to install:

This is all that is needed from the Onboard side to generate a certificate. Please see how to install the server certificate as well as the user certificate (.p12) file on various flavors of clients at the external link here: https://uniluug.org/wiki/Template:EAP-TLS