Hi aruba-friends,
i´m near a nervous breakdown to be true.
But first things first.
I have 2 Problems which i don´t know how to get by.
The Environment is as follows:
1x Aruba 2930F with DUR for 802.1x and MAC-Auth
1x IGEL Thinclient (Port 3)
1x PC (Windows 10 with PKI certificate) (Port 4)
1x Extreme Networks access-point (please don´t throw rocks) (Port 7)
1x MSM 460 AP (Port 6)
1x Clearpass-Cluster
The Switch has Firmware 16.09.003
1st Problem:
The Ports on the switch are configured as authenticator and mac-based.
The Ports are configured as authenticator with "no" client limit which means configured in "port-based" mode.
Problem:
The clients get authenticated by cppm but the client isn´t able to receive a dhcp lease.
Putting the port in "user-based" with "client-limit 1" solves the problem and the client get´s authenticated also but can request a dhcp lease.
There are no restricting ACL involved on the cppm.
Question:
Shouldn´t this be the exactly behavior in port based mode also?
Problem 2:
Actually we use HP MSM and Extreme network APs in our environment.
The APs are MAC-authenticated.
Manually configured (and without DUR) this looks like this:
vlan xxx untagged int 1 (where the access-point is managed)
vlan yyy tagged 1 (Breakout-VLAN for a specific SSID)
vlan zzz tagged 1 (Breakout-VLAN for another specific SSID)
The clients connecting to the specified VLANs get authenticated against our old radius server.
As soon as i enable mac-auth in the port and the AP getting the same vlan tag/untag config as DUR all clients connected to the AP try to authenticate against cppm which should not happen at the moment.
So the Radius requests are sent to the cppm instead of the AP configured radius server.
This can be usefull in sometimes later - but right now i just want my port to put the AP only dynamicly into the right tagged/untagged vlan configuration without trying to do the client radius authentication.
Plz help!
Here are my Port-Config snippets:
To Problem 1/2 - as an Example:
interface 1
untagged vlan 666
lldp admin-status disable
no cdp enable
aaa port-access authenticator
aaa port-access mac-based
aaa port-access mac-based addr-moves
aaa port-access auth-order authenticator mac-based
aaa port-access auth-priority authenticator mac-based
loop-protect
exit
port-access summary:
| Authenticator | Web Auth | MAC Auth | Local MAC
Port | Enable Mode Limit | Enable Limit | Enable Mode Limit | Enable Limit
----- - ------ ----- ----- - ------ ----- - ------ ----- ----- - ------ -----
1 | Yes Port 0 | No 1 | Yes User 1 | No 1
2 | Yes Port 0 | No 1 | Yes User 1 | No 1
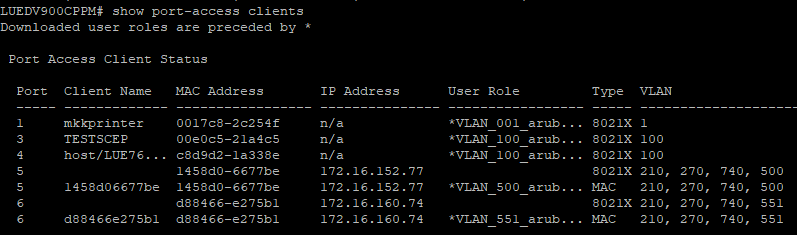
As you can see at port 5/6 the both MSM and Extreme APs also submit the Wifi-Adapters MAC-Address which is "nuts" ...
And as you can see, the clients on 3/4 received the correct cppm profile - but aren´t able to get an ip address.
If i configure the ports as "user-mode" they get an ip at once.
(aaa port-access authenticator 3,4 client limit 1)
Regards
Hec
- What the hec?