Requirement:
ArubaOS-Switch
Solution:On the VLAN interfaces of a routing switch, dynamic ARP protection ensures that only valid ARP requests and responses are relayed or used to update the local ARP cache. ARP packets with invalid IP-to-MAC address bindings advertised in the source protocol address and source physical address fields are discarded. A routing switch maintains a DHCP binding database which is used for DHCP and ARP packet validation.
In the following example, switch Rack2sw1 is configured as a DHCP-Client, switch Rack2sw3 is configured as a DHCP-Server and switch Rack2sw2 is configured for DHCP-Relay, ARP-Protect and DHCP-Snooping. Trunk Trk23 is enabled a trusted ARP-Protect interface as part of testing.
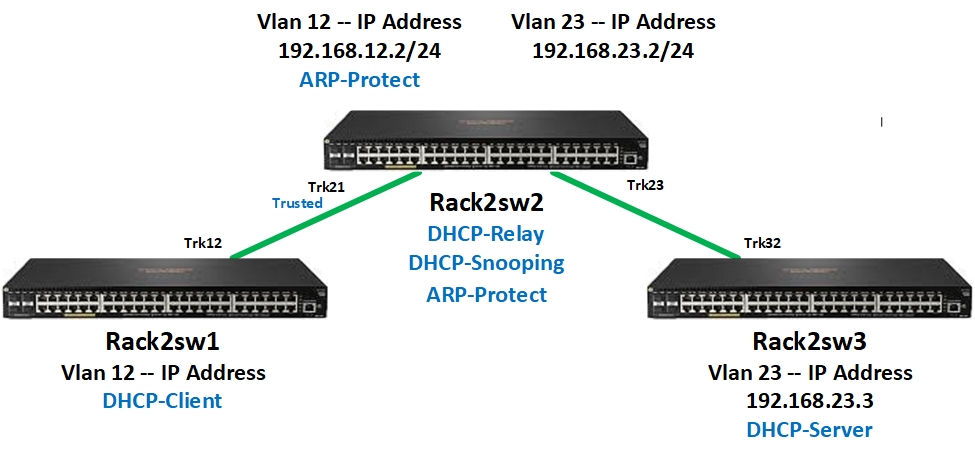
Configuration:
---------- DHCP Snooping Configuration ----------
Rack2sw2(config)# vlan 12 dhcp-snooping
Rack2sw2(config)# dhcp-snooping
Rack2sw2(config)# dhcp-snooping authorized-server 192.168.23.3
Rack2sw2(config)# interface trk23 dhcp-snooping trust
---------- DHCP Relay Configuration ----------
Rack2sw2(config)# vlan 12 ip helper-address 192.168.23.3
---------- ARP Protect Configuraiton ----------
Rack2sw2(config)# arp-protect
Rack2sw2(config)# arp-protect vlan 12
Verification
---------- DHCP Snooping Bindings ----------
Rack2sw2# show dhcp-snooping binding
MacAddress IP VLAN Interface Time Left
--------------------- --------------- ---- --------- ---------
2c59e5-5f6f00 192.168.12.100 12 Trk21 7114
---------- ARP Protect Verification ----------
Rack2sw2# show arp-protect
ARP Protection Information
ARP Protection Enabled : Yes
Protected Vlans : 12
Validate :
Port Trust
----- -----
Ports 5-48,Trk21,Trk23 are untrusted
Rack2sw2(config)# show arp-protect statistics 12
ARP Protection Counters for VLAN 12
ARPs forwarded : 0 Bad Sender/Target IP : 0
Bad bindings : 0 Source/Sender MAC mismatches : 0
Malformed pkts : 0 Dest/Target MAC mismatches : 0
---------- ARP Protect Testing ----------
Testing is accomplished by clearing the DHCP-Snooping binding for the IP address 192.168.12.100, and then executing a ping command on switch Rack2sw1. The ping fails, and the ARP-Protect counter “Bad Bindings” increments.
Rack2sw2# clear dhcp-snooping binding all
Warning: Execution of this command results in clearing of dynamically learnt
DHCP Snooping entries from the binding table on this switch. Since the
DHCP Server and the DHCP Clients would not be aware of this change, this can
have side effects.
Do you want to continue (y/n)? y
Rack2sw1# ping 192.168.12.2
Request timed out.
Rack2sw2# show arp-protect statistics 12
ARP Protection Counters for VLAN 12
ARPs forwarded : 0 Bad Sender/Target IP : 0
Bad bindings : 3 Source/Sender MAC mismatches : 0
Malformed pkts : 0 Dest/Target MAC mismatches : 0
The configuration for trunk Trk21 is ARP-Protect trusted which allows the ARP response to the ping from Rack2sw1.
Rack2sw2(config)# interface trk21 arp-protect trust
Rack2sw2# show arp-protect
ARP Protection Information
ARP Protection Enabled : Yes
Protected Vlans : 12
Validate :
Port Trust
----- -----
Trk21 Yes
Ports 5-48,Trk23 are untrusted
Rack2sw1# ping 192.168.12.2
192.168.12.2 is alive, time = 5 ms