Requirement:
When a port on the switch with tagged VLAN is mirrored to a Windows PC the dot1q header may not be displayed in Wireshark.
Only some ethernet NIC/driver will allow to capture dot1q header directly on Windows. In some cases changes need to be made to the registry to enable display of VLAN tagging.
Here is a technique that can be used to capture the dot1q header on Windows PC without any registry changes.
A Windows PC with Wireshark and IP connectivity to the switch is required for this task.
Solution:
ArubaOS-Switch supports remote mirroring feature which can be used in this scenario. The switch will send the mirrored packets along with a GRE encapsulation to the destination PC.
The source IP (an interface on the switch) and the IP address of the remote PC (which has Wireshark running) needs to be specified along with a UDP port number.
This UDP port number will later be used in Wireshark to Decode the packet.
Configuration:
- Below is the configuration that is required on the switch to enable remote mirroring.
mirror <id> remote ip <Source VLAN Interface IP on the switch> <UDP port number for encapsulation> <IP address of the PC running Wireshark>
interface <id> all both mirror <id>
Sample configuration to enable mirror on interface 1
Aruba-3810M-40G-8SR-PoEP-1-slot# configure terminal
Aruba-3810M-40G-8SR-PoEP-1-slot(config)# mirror 2 remote ip 10.0.0.1 5454 10.0.0.10
The destination switch must be configured before proceeding.
Has the remote switch been configured (y/n)? y
Aruba-3810M-40G-8SR-PoEP-1-slot(config)#
Aruba-3810M-40G-8SR-PoEP-1-slot(config)# interface 1
Aruba-3810M-40G-8SR-PoEP-1-slot(eth-1)# monitor all both mirror 2
Aruba-3810M-40G-8SR-PoEP-1-slot(eth-1)# end
Aruba-3810M-40G-8SR-PoEP-1-slot#
Aruba-3810M-40G-8SR-PoEP-1-slot# sho monitor 2
Network Monitoring
Session: 2 Session Name:
Mirror Destination: IPv4
UDP Source Addr UDP port UDP Dest Addr Status
--------------- -------- --------------- --------
10.0.0.1 5454 10.0.0.10 active
Monitoring Sources Direction Truncation Mirror Policy
------------------ --------- ---------- -------------
Port: 1 Both No -
Open Wireshark and start capture for the interface corresponding to the destination IP on the switch
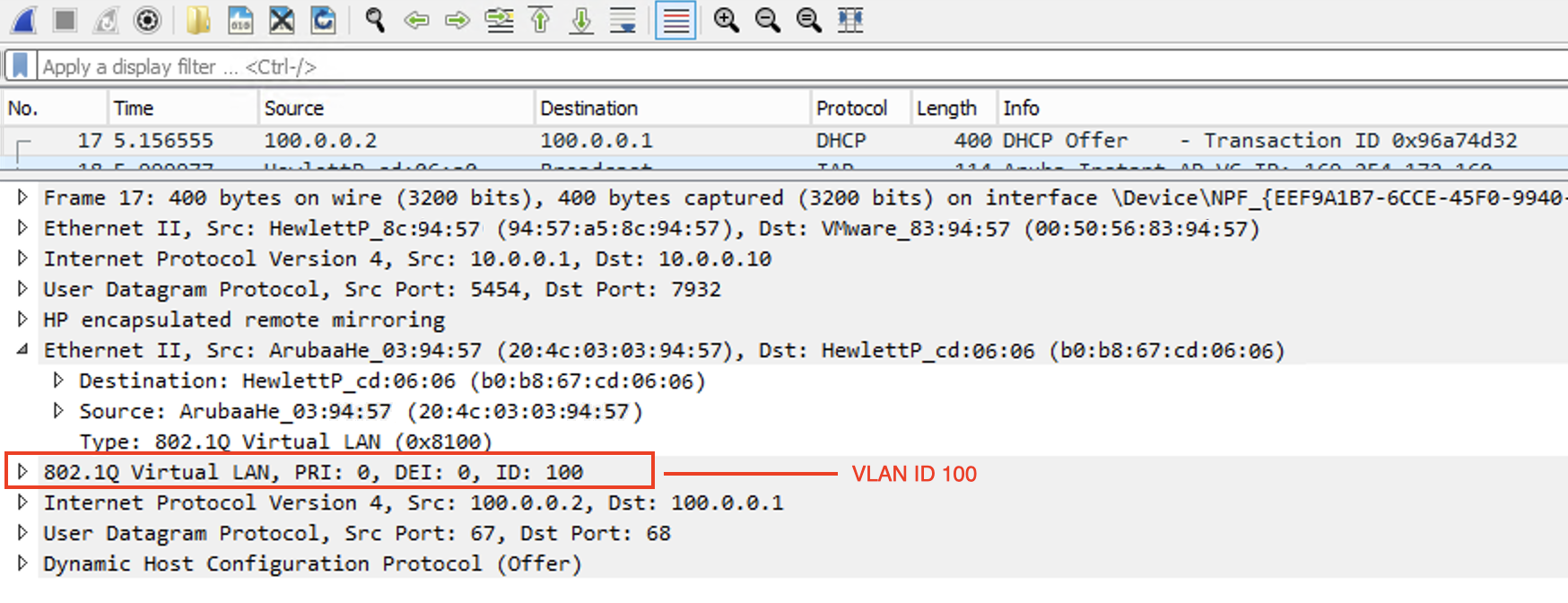
UDP packets with destination port 5454 can be seen, as displayed in the screenshot below

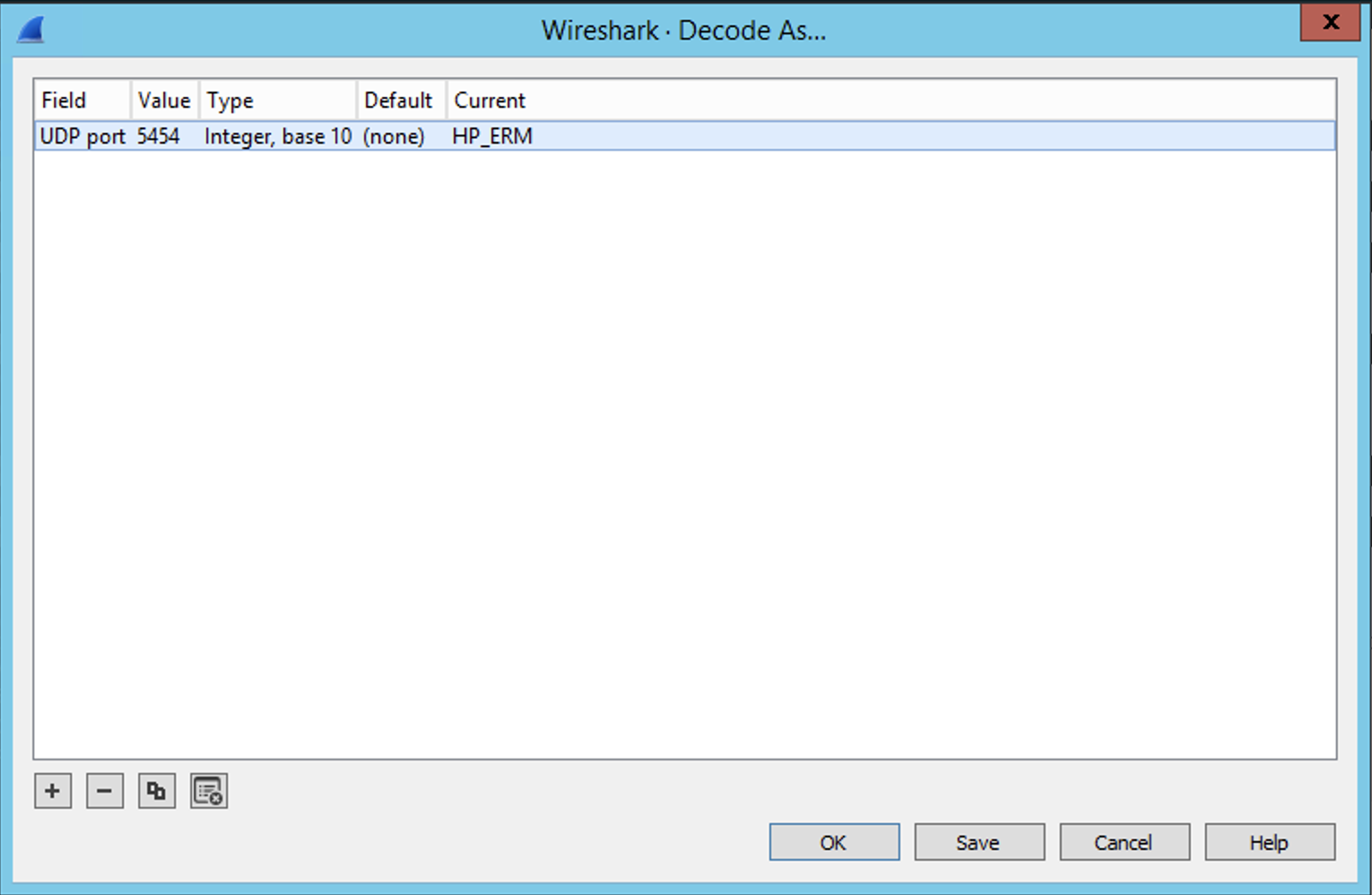
Right click on the UDP packet and click on 'Decode As...'
Select 'HP_ERM' from the dropdown in 'Current' field. Please refer below screenshot.
Verification
After the packets are decoded, Wireshark will decode and display the packets

Below is the screenshot of a packet sent by the switch with dot1q header information. The monitored interface on the switch is configured to tag packets for VLAN100.